The Katchatheevu controversy (GS Paper 2, International Relation)
Why in news?
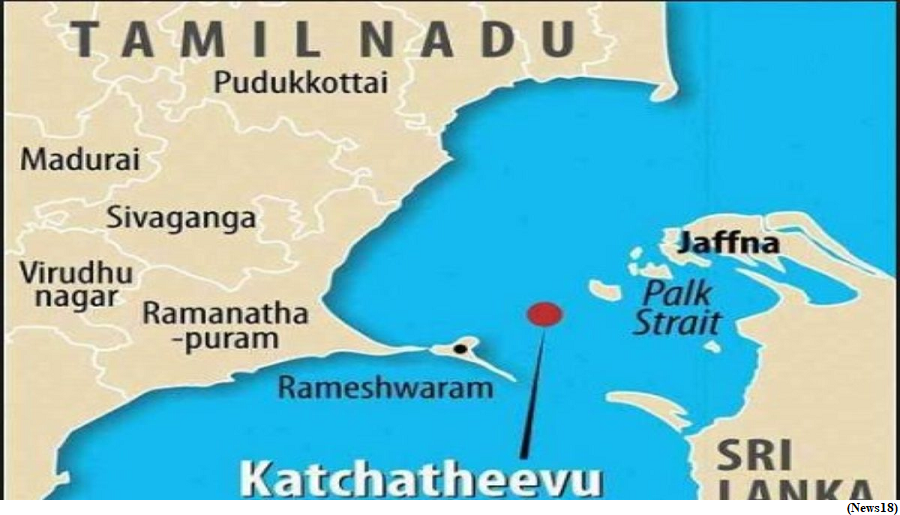
- Recently, the Tamil Nadu Chief Minister revived the debate over Katchatheevu, an uninhabited and barren 285 acre islet about 14 nautical miles off Rameswaram.
- He reiterated the demand for retrieval of the islet from Sri Lanka, which will, according to him, put a permanent end to the problems of fishermen of the State.
When did Katchatheevu become a part of Sri Lanka?
- During June 26-28, 1974, the then Prime Ministers of India and Sri Lanka, Indira Gandhi and Sirim R.D. Bandaranaike, signed an agreement to demarcate the boundary between the two countries in the historic waters from Palk Strait to Adam’s Bridge.
- A joint statement issued on June 28, 1974, stated that a boundary had been defined “in conformity with the historical evidence, legal international principles and precedents.”
- It also pointed out that “this boundary falls one mile off the west coast of the uninhabited” Katchatheevu.
How important is Kachatheevu?
- Fisherfolk of the two countries have been traditionally using the islet for fishing.
- Though this feature was acknowledged in the 1974 agreement, the supplemental pact in March 1976 made it clear that fishermen of the two countries “shall not engage” in fishing in the historic waters, territorial sea and exclusive zone or exclusive economic zone of either of the countries “without the express permission of Sri Lanka or India.”
- Certain sections of political parties and fisherfolk in Tamil Nadu believe that the retrieval of Katchatheevu would resolve the problem of fishermen having to illegally cross the International Maritime Boundary Line.
- The fishermen of the Northern Province in Sri Lanka say that this would only add to their suffering from the adverse impact of T.N. fishermen using the fishing method of bottom trawling on their territorial waters.
What triggered the negotiations between India and Sri Lanka?
- Sri Lanka claimed sovereignty over Kachatheevu on the ground that the Portuguese who had occupied the island during 1505-1658 CE had exercised jurisdiction over the islet.
- India’s contention was that the erstwhile Raja of Ramnad (Ramanathapuram) had possession of it as part of his zamin.
How was the 1974 pact received?
- The present demand for the Katchatheevu retrieval traces its origin to the opposition that the pact generated in 1974.
- During the debates in both Houses of Parliament in July 1974, most of the Opposition including the Dravida Munnetra Kazhagam (DMK), All India Anna Dravida Munnetra Kazhagam (AIADMK), Jan Sangh, Swatantara and the Socialist Party, staged walk outs in the two Houses.
- Former Prime Minister Atal Bihari Vajpayee, who was the Jan Sangh’s leader, had contended that the decision to transfer the islet had been taken “behind the back” of the people and Parliament.
- The then Chief Minister M. Karunanidhi, in 1973 had urged Indira Gandhi that the popular feeling was in favour of retaining Katchatheevu which “belonged to India and not to Tamil Nadu alone”.
When did the issue emerge again?
- The Katchatheevu issue was revived in August 1991 with the then Chief Minister Jayalalithaa demanding retrieval during her Independence Day address.
- She later modified her demand to one of getting the islet back through “a lease in perpetuity.”
What has the Centre said?
- In August 2013, the Union government told the Supreme Court that the question of retrieval of Kachchatheevu from Sri Lanka did not arise as no territory belonging to India was ceded to Sri Lanka.
- It contended that the islet was a matter of dispute between British India and Ceylon (now Sri Lanka) and there was no agreed boundary, a matter of which was settled through 1974 and 1976 agreements.
- In December 2022, the Centre pointed that Katchatheevu “lies on the Sri Lankan side of the India-Sri Lanka International Maritime Boundary Line.” It added that the matter was sub-judice in the Supreme Court.
What is RBI’s new pilot for frictionless credit?
(GS Paper 3, Economy)
Why in news?
- Recently, the RBI commenced a pilot programme endeavouring to evaluate the feasibility and functionality of the ‘Public Tech Platform for Frictionless Credit’.
- The suggested platform would strive to “enable delivery of frictionless credit by facilitating seamless flow of required digital information to lenders.”

What is the platform for?
- Digital delivery of credit (delivering credit/loans though digital means) or any loan is preceded by a process of scrutiny known as credit appraisal.
- The process attempts to evaluate and accordingly predict the prospective borrowers’ ability for repayment of credit/loan and adhering to the credit agreement. This pre-disbursal process is particularly important for banks since it would in turn determine their interest income and impact on the balance sheet.
- The data required for the process rests with different entities like central and state governments, account aggregators, banks, credit information companies, and digital identity authorities.
- Thus, being in separate systems, it creates “hindrances in frictionless and timely delivery of rule-based lending.
Pilot Project:
- To facilitate “frictionless” and “timely delivery” of loans, the central banking regulator had instituted a pilot project for the digitalisation of Kisan Credit Card (KCC) loans, of less than ₹1.6 lakh, in September 2022.
- It tested “end-to-end digitalisation of the lending process in a paperless and hassle-free manner”.
- The pilot is currently ongoing in select districts of Madhya Pradesh, Tamil Nadu, Karnataka, Uttar Pradesh and Maharashtra.
- It provides for “doorstep disbursement of loans in assisted or self-service mode without any paperwork.”
What is this pilot about?
- The platform is premised around the learnings from all the ongoing programmes, and further expands the scope to all types of digital loans. The public platform will be developed by its wholly owned subsidiary, the Reserve Bank Innovation Hub (RBIH).
- The proposed end-to-end platform will have an open architecture, open Application Programming Interfaces (API) and standards, to which all financial sector players would be able to connect seamlessly in a ‘plug and play’ model.
- With the participation from certain banks, the platform would extend its focus also towards dairy loans, MSME loans (without collateral), personal loans and home loans.
- It is expected to link with services like Aadhar e-KYC, Aadhar e-signing, land records from onboarded State governments, satellite data, PAN validation, transliteration, account aggregation by account aggregators (AAs), milk pouring data from select dairy co-operatives, and house/property search data.
What purpose does it serve?
- The improved access to information provides the basis for fact-based and quick credit assessments. It ensures that credit is extended to a larger set of borrowers with good credit history.
- The borrowers too would benefit by the resulting lower cost of accessing capital, which would translate into productive investment spending. Availing formal credit may entail multiple visits to the bank alongside cumbersome documentation.
- This translates to higher operational costs for lenders which may also get distributed to borrowers.
How AI is used to increase the frequency of Acoustic Side Channel Attacks
(GS Paper 3, Science and Technology)
Why in news?
- Recently, a research paper by the ethics committee of Durham University, U.K., revealed that Artificial Intelligence (AI) can be used to decode passwords by analysing the sound produced by keystrokes.
- The paper is titled as “A Practical Deep Learning-Based Acoustic Side Channel Attack on Keyboards”.
- The study highlighted the accuracy of Acoustic Side Channel Attacks (ASCA) when state-of-the-art deep learning models were used to classify laptop keystrokes and their mitigation.

What are ASCA?
- Side Channel Attacks (SCAs) are a method of hacking a cryptographic algorithm based on the analysis of auxiliary systems used in the encryption method.
- These can be performed using a collection of signals emitted by devices, including electromagnetic waves, power consumption, mobile sensors as well as sound from keyboards and printers to target devices. Once collected, these signals are used to interpret signals that can be then used to compromise the security of a device.
- In an ASCA, the sound of clicks generated by a keyboard is used to analyse keystrokes and interpret what is being typed to leak sensitive information.
- The sound of keyboard clicks has become less profound with devices making use of non-mechanical keyboards, the technology with which the acoustics can be accessed and processed has also improved drastically.
- Additionally, the use of laptops has increased the scope of ASCAs as laptop models have the same keyboard making it easier for AI-enabled deep learning models to pick up and interpret the acoustics.
How accurate are Acoustic Side Channel Attacks?
- The research investigated the use of audio recordings taken from Zoom video conferencing calls, smartphone microphones, and off-the-shelf equipment and algorithms to launch ASCA attacks.
- The study found that when trained on keystrokes by a nearby phone, the classifier achieved an accuracy of 95%, the highest accuracy seen without the use of a language model.
- When a deep learning model was trained on the data with default values, the model was able to acquire a meaningful interpretation of the data.
Are such attacks new?
- ASCA attacks are not new and have been around since 1950 when acoustic emanations of encryption devices were used to crack their security.
- Additionally, the United States National Security Agency (NSA) declassified documents listed acoustic emanations as a source of compromise in 1982.
- With the increasing use of AI and the accuracy with which deep learning models can recognise and analyse keystrokes, the threat from ASCA has resurfaced.
- Especially since users may not take ample precautions while typing in sensitive information including banking data and password on their laptops in public spaces like coffee shops, airports, and cafes.
How can users protect against ASCAs?
- While there is no explicit means of defence against ASCAs, simple changes to typing could reduce the chances of attacks.
- Using touch-based typing can also reduce the chances of successful keystroke recognition from 64% to 40%, making it more difficult for threat actors to leak sensitive information.
- Additionally, changes in typing style and creating stronger passwords that use a combination of upper- and lower-case alphabets can make it more difficult for criminals to launch successful ASCA attacks; the study found that even deep learning models had a difficult time recognising the use of shift key to change the case of alphabets when typing.
- Users should also avoid the use of easily recognisable phrases which can make it easier for AI models to predict the text.




